Ethical Hacking vs Penetration Testing is a crucial comparison in cybersecurity careers, as these overlapping roles often lead to confusion. This article will clarify the distinctions between ethical hacking and penetration testing, outlining their unique responsibilities and how each contributes to strengthening cybersecurity. Additionally, we’ll explore the role of organizations like EC-Council in certifying professionals in these fields. Understanding Ethical Hacking vs Penetration Testing is essential for anyone entering cybersecurity.
The two roles do share certain similarities: Both roles focus on identifying vulnerabilities in IT systems and work to prevent different types of cyberattacks. The two professions also have comparable high salaries and growth potential. The U.S. Bureau of Labor Statistics (2021) groups penetration testers and ethical hackers together under the umbrella of “information security analysts,” an employment category with projected growth of 33% between 2020 and 2030. According to PayScale (2021, 2022), the average annual salary for an ethical hacker is $80,000, while the average annual salary for a penetration tester is $87,750.
However, despite these similarities, ethical hacking and penetration testing are separate career paths that involve different skill sets. Understanding the difference between the two roles is crucial, particularly for cybersecurity professionals seeking additional credentials, such as EC-Council’s Certified Ethical Hacker (C|EH) certification.
Ethical Hacking vs Penetration Testing: The Role of a Penetration Tester
In the broader context of Ethical Hacking vs Penetration Testing, penetration testers focus on targeted system weaknesses. A penetration test is a coordinated assessment carried out by an independent team contracted by an organization, with the client organization defining the scope of the test. The test scope describes what systems need to be tested and what methods the tester will use. The penetration tester then attempts to exploit the client’s system according to the scope outlined by the client. The tester identifies and exploits any weaknesses they encounter to quantify the risk these vulnerabilities pose to the client.
After testing is complete, the penetration tester prepares a report that includes an executive summary of the test parameters along with vulnerability classification documents and suggestions for remediation. Testers generate a risk score by pairing the penetration test report with the business value of the targeted systems to calculate the level of risk that a cyberattack would pose to the client. The report’s end goal is to provide the client and their stakeholders with information about any security vulnerabilities in the system and outline the actions required to resolve those vulnerabilities.
Penetration testing has many applications in cybersecurity, security maturity modeling, and risk management. Businesses frequently use penetration testing to identify vulnerabilities in their security infrastructures that cybercriminals can exploit when launching cyberattacks (EC-Council, 2021c). Organizations also use penetration testing for audit compliance to ensure that their operations adhere to relevant laws, regulations, and company policies. For example, if a company is subject to SEC filing requirements, an independent security audit using penetration testing is needed to validate the integrity of the organization’s security infrastructure (EC-Council, 2021a).
Ethical Hacking vs Penetration Testing: The Role of an Ethical Hacker
While penetration testers focus solely on carrying out penetration tests as defined by the client, ethical hacking is a much broader role that uses a greater variety of techniques to prevent different types of cyberattacks (EC-Council, 2021b). Ethical hackers may be involved in:
- Web application hacking
- System hacking
- Web server hacking
- Wireless network hacking
- Social engineering tests
- Forming blue and red teams for network exploitation attacks
An ethical hacker’s responsibilities are not restricted to testing a client’s IT environment for vulnerabilities to malicious attacks. Ethical hackers also play a crucial role in testing an organization’s security policies, developing countermeasures, and deploying defensive resolutions to security issues. When employed by a company as in-house cybersecurity professionals, ethical hackers may help build the foundations of an organization’s cybersecurity system or augment app, tool, and protocol communication networks (EC-Council, 2021a).
Although they rely on penetration testing to uncover vulnerabilities, it represents just one among many tools in their arsenal to safeguard systems from cyberattacks. In short, an ethical hacker’s methodologies and roles are more varied than those of a penetration tester. Ethical hackers apply a variety of methods beyond traditional penetration testing in Ethical Hacking vs Penetration Testing. Understanding these broader responsibilities is key when evaluating a career path in Ethical Hacking vs Penetration Testing.
The Core Differences Between Ethical Hacking and Penetration Testing
Below is a summary of the key differences between a penetration tester and an ethical hacker (EC-Council, 2021a).
- Penetration testers assess the security of a specific aspect of an information system according to an outlined scope. Ethical hackers carry out many types of cyberattacks on an entire system using multiple attack vectors without being restricted by a scope document.
- Penetration testers carry out a one-time, limited-duration engagement. Ethical hackers have a continuous engagement that generates more in-depth and comprehensive results.
- Penetration testers need a robust knowledge of the domain or area that their penetration tests will target. Ethical hackers need detailed knowledge of hacking tactics, techniques, and procedures so that they can imitate a cybercriminal’s steps.
- Penetration testers are not responsible for the client’s security configuration and incident handling. Ethical hackers are required to assist blue teams and incident handling teams in incident containment and validation for different types of cyberattacks.
- Penetration testers must be proficient in writing foolproof reports. Ethical hackers generally do not need to be well versed in report writing.
In the context of Ethical Hacking vs Penetration Testing, ethical hackers use penetration testing as one of their many tools for diagnosing security issues in a client’s security system. However, ethical hackers focus more heavily on building and improving a client’s information security system. In contrast, penetration testers are devoted solely to carrying out tests that identify and exploit weaknesses in a client’s IT environment and providing detailed reports on all identified vulnerabilities, the risk those vulnerabilities pose to the organization, and suggestions for remedial action. A penetration tester is not involved in fixing identified vulnerabilities; likewise, ethical hackers do not produce penetration test reports for clients. This distinction highlights the core difference in Ethical Hacking vs Penetration Testing.
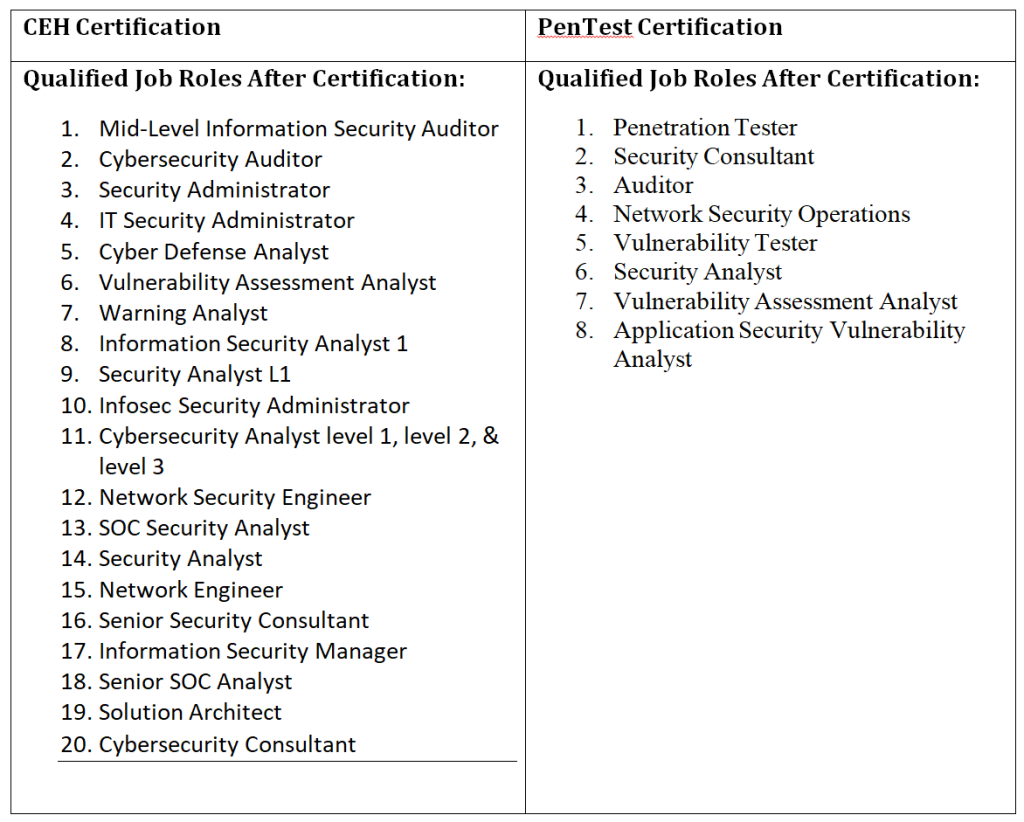
Earn Globally Recognized Cybersecurity Credentials
A career in either penetration testing or ethical hacking offers engaging and rewarding opportunities in an industry that promises employment stability and growth. At EC-Council, we offer globally recognized penetration testing and ethical hacking certification programs, including the C|EH, C|EH Master, Certified Penetration Testing Professional (C|PENT), and Licensed Penetration Tester (L|PT) Master. Get certified and move forward in your career as a cybersecurity professional today! Certifications related to Ethical Hacking vs Penetration Testing boost your credibility and job prospects. Many professionals compare Ethical Hacking vs Penetration Testing to decide which path aligns best with their long-term cybersecurity goals.
Choosing between Ethical Hacking vs Penetration Testing as a career path depends on your interests and skill sets, but both fields offer exciting opportunities and vital roles in cybersecurity.

Take the Next Step with Bilişim Academy
Whether you want to specialize in Ethical Hacking vs Penetration Testing, Bilişim Academy offers tailored training programs. Ready to pursue a career in ethical hacking or penetration testing? At Bilişim Academy, we offer hands-on cybersecurity training, including EC-Council’s Certified Ethical Hacker (C|EH) and penetration testing programs.
Learn from industry experts, access real-world labs, and get certified.
Join our cybersecurity training programs today and start building your future in information security.
References
EC-Council. (2021a). CEH vs. PenTest+. https://www.eccouncil.org/ceh-vs-pentest/
EC-Council. (2021b). What is ethical hacking? https://www.eccouncil.org/ethical-hacking?/
EC-Council. (2021c). What is penetration testing? https://www.eccouncil.org/what-is-penetration-testing/
PayScale. (2021, September 26). Average ethical hacker salary. https://www.payscale.com/research/US/Job=Ethical_Hacker/Salary
PayScale. (2022, January 25). Average penetration tester salary. https://www.payscale.com/research/US/Job=Penetration_Tester/Salary
U.S. Bureau of Labor Statistics. (2021). Information security analysts. In Occupational outlook handbook. https://www.bls.gov/ooh/computer-and-information-technology/information-security-analysts.htm



